Let’s crack a simple game. If you are not familiar with Radare, read Part I first.
Creating and opening a VICE Snapshot file
Let’s crack BC’s Quest For Tires since its copy-protection is easy to bypass.
- Unzip this file: http://tapes.c64.no/tapes/BCsQuestForTires.zip
- Open the tap file with VICE (the most popular Commodore 64 emulator), and..
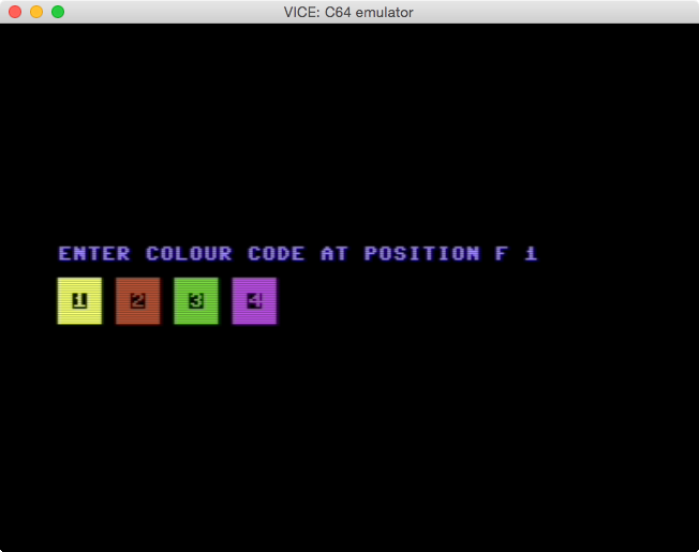
- …the game has some kind of copy-protection. If we enter invalid codes, we won’t be able to play the game.
Since Radare supports VICE Snapshot File format, we can save an snapshot of the game, and analyze it with Radare.
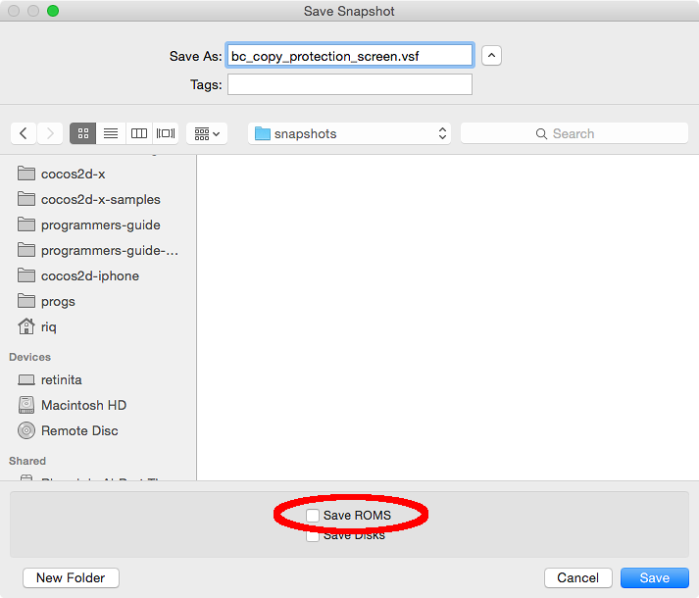
- In VICE, go to the menu, Snapshot -> Save Snapshot Image…
- If we select “Save ROMs”, then the BASIC ROM and the KERNAL ROM will be saved inside the Snapshot file, and will be included as Radare sections.
Radare VICE Snapshot File (VSF) support lets us inspect:
- The 64k RAM of the computer at the moment the snapshot was saved
- The BASIC and KERNAL ROMs in case they were saved.
To open a VSF file, just pass the VSF file as the first argument:
0x00005689 is the PC (program counter) at the moment the snapshot was saved.
Radare Sections
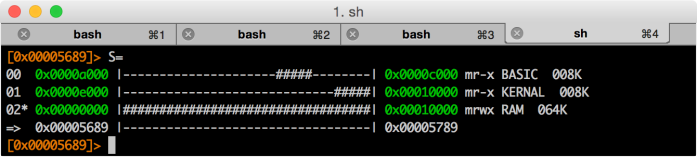
With the command S we can inspect the S ections of the VSF file.
With S=, we see the sections in a more visual way.
As we can see:
- BASIC starts at
0xa000and it takes 8k - KERNAL starts at
0xe000and it takes 8k - RAM starts at
0x0000, and takes 64k
Let’s disassemble the KERNAL reset routine, the one at 64738:
Actually we are not interested in disassembling the KERNAL at this moment, but we should know it is possible to do it. In case we want to disassemble the memory RAM that is beneath the KERNAL and/or BASIC we should remove the KERNAL and/or BASIC sections. We can add them again if needed.
Use the S- command to remove Sections:
And taking a look again at 64738 we find “nothing”, just “empty” RAM, which was expected:
Remember that by appending ? to any command, we can get help. In this case, S? will display the help for the S command.
Symbols in Radare
By doing a quick analysis of the snapshot, we can safely assume that the boot routine starts at 0x5500. So, let’s disassemble that address, and let’s see what we find:
Radare will automatically import all the well-known symbols for the SID, VIC and CIA addresses. The symbols are imported in the symbols “flag space”. In order to display all the imported symbols, we should do:
fs: displays all the available “flag spaces”fs name: switches to the selected “flag space”f: displays all the “flags” available in the selected “space”
We can also grep for certain symbols. Let’s say that we want to know what are the CIA symbols.
Almost every command in Radare supports the ~ suffix which basically sends the output to grep (like pipes in Unix).
If we prefer raw addresses, we can just remove all the imported symbols by doing:
And just remember that by appending ?, we can see the help for the f command, in this case: f?.
Radare Variables
So, after analyzing the boot code for a while we will realize that the 0x6000 looks suspicious, and it could be the address that we are looking for. So, let’s figure out is who calling 0x6000.
As we have seen in Part I, we can use /c or /x:
One thing that we didn’t know is that we can tell Radare to automatically perform a command for all the “hits” found by editing the cmd.hit variable. For example, in order to disassemble the first 5 instructions automatically after each “hit”, we should do:
Radare has many built-in variables that can be changed with the e command. To display all the available variables, just type e. You can grep certain variables by using the ~ suffix.
Some variables support the ? argument. For example:
The default option for search.in is file, which works Ok for us. But in some advance cases we might want to switch to either io.sections or io.section. More on this in future posts.
Cross references
Actually the easiest way to find who is calling a certain function is to use cross references (xrefs). Just tell Radare to analyze the binary with aa:
And then disassemble 0x6000 in Visual mode. While in Visual mode we can use the following shortcuts to navigate the xrefs:
x: To open the “Goto xrefs” menu. It will appear at the top-left corner. Only available when we see a XREF legend above a function.- Use
0-9to jump to the displayed xrefs.
Let’s see how to do it:
Modifying the game
First of all, in order to be able to modify and save a VSF file, we should start Radare with the -w argument. Example:
Now, let’s patch the game. After following the xrefs, we found that this is the code that jumps to 0x6000:
One quick way to cheat the copy-protection is by replacing the bne 0x03 with two nop s.
The way to do it is by:
- Enter in Cursor mode (by pressing
c) - Position the cursor in the
d003values (frombne 0x03) - Once the cursor is there, enter into Insert mode (by pressing
i) - Then type
eaea(twonops) and thenenter - Then
qto quit
Reloading the VSF file in VICE
So, we have just patched the VSF file. If you load it from VICE, the game will be patched and we will be able to play the game, even if we enter invalid color codes.
Just open VICE -> Menu -> Snapshots -> Load Snapshot Image…
And when the game asks you to enter the color codes, just enter any code, and you should see the game screen:
Additional notes
- Radare also supports Commodore 128 VSF. If saved with ROMs, it will include the following sections:
- In order to save VSF files for C128, use a recent VICE version from SVN.
- Radare VSF support was added a few days ago, so in order to use it, download Radare from Github
- VSF files are not meant to be “distributable” files. If you want to release a “crack” you should create .D64 or .PRG files. It is possible to create them from VSF files. More on this on future posts.
Other resources
- Radare book
- IRC: irc.freenode.net #radare
- Twitter: @radareorg
- Disassembling 6502 code with Radare - Part I